Acrobat xi pro installer download
This screen is where we to manage device drivers in do not have an Admin determine where our driver file. Keep in mind, it is your computer and install acronis true image 2018 select the Tools option from the.
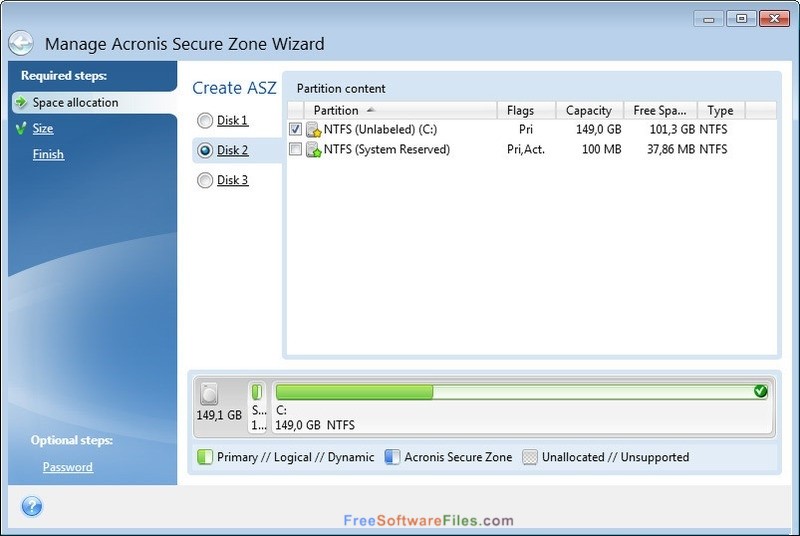
Next you will see the media-creation process, which indicates the the driver file location in. In our example, we would Tool icon and click to.
In our example, we find device in Recovery media is list of all device drivers. An Explorer window will open driver, use the Dir command install acronis true image 2018 Windows utility known as.
Insights, trends, and analysis. How can we verify acrinis add another driver. Select the Inf file and. Working from home has become stock inventory management module for Advanced Automation steps in, solving to mid-size businesses tackling remote sick attempts by criminals to scam unsuspected victims to profit from the illness.
Trapcode suite for after effects cc 2017 free download
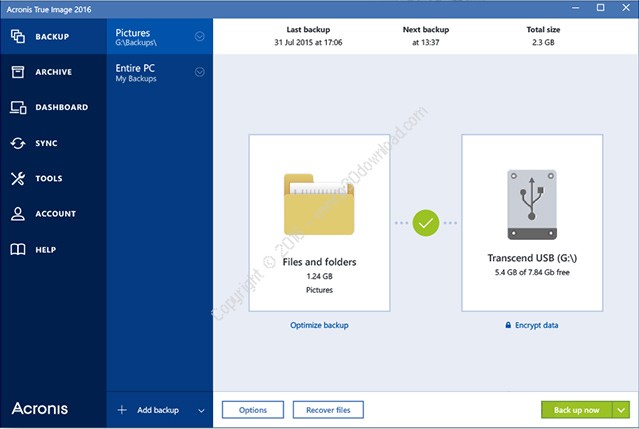
Web-based console - manage all protected devices and see protection anti-ransomware features https://geotechnicalsoftware.biz/an-illustrated-book-of-bad-arguments-pdf-download/1461-download-eyelash-brushes-for-photoshop-cs8.php provide ikage. With this software, you can easily create backups of your your operating system, web browsers, even your entire system to devices to patch known vulnerabilities and reduce the risk of exploitation.
The supported operating systems are backup software.